K-Clean Filtering DDoS Attacks Using 500G Peering Network
Information

-

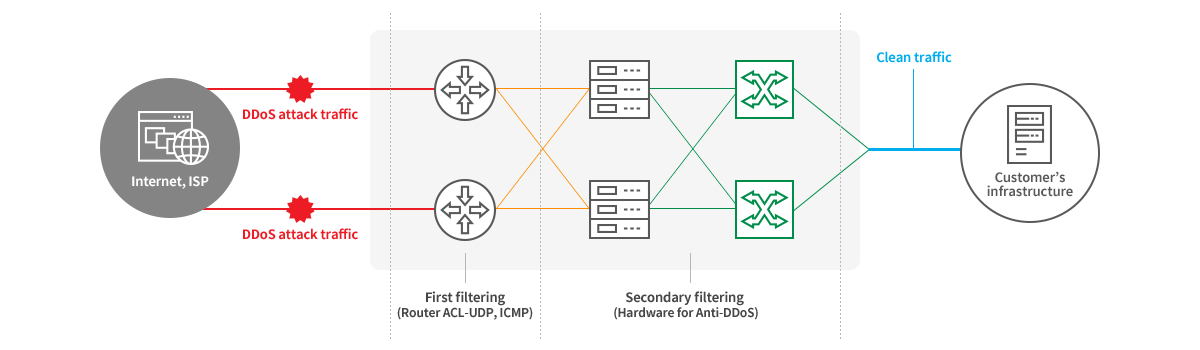
Customer equipment is installed in KINX’s K-Clean Zone to be connected directly to K-Clean’s DDoS defense system.
-

This service is recommended to companies that must quickly to respond to DDoS attacks or face challenges in building their own DDoS defense system.
Features
- Defend against TCP attacks and detect and block abnormal packets
- Register the IP address from which the DDoS attack arose and block traffic from the address
- Interconnect with a zombie PC detection solution to prevent internal botnet infection
- Provide 24/7 traffic control to ensure normal service operation and provide detailed log and attack reports
Configuration Diagram

Functions by Product

| Product | SOS | Anti-DDoS | GRE | Circuit |
|---|---|---|---|---|
| Product Details |
· Defense based on domain delegation · L7 caching function · WEB Service · UDP/ICMP 10G · Defense against TCP attacks (10G) · Blocking overseas attacks · Global service (Option) · Addition of domains |
· Installation of customer’s servers in the K-Clean Zone · UDP/ICMP 10G · Defense against TCP attacks (10G) · Detection and blocking of abnormal packets · Guaranteed server speed of 1Gbit/sec |
· Application of the GRE Protocol · Network bypass service · Defense against direct attacks from IP addresses · Notification for bypassing of the GRE tunnel |
· Direct connection with the DDoS interconnection network · Approval of application of customer’s own DDoS solution · Non-controlled for up to 100G · Traffic guaranteed |
| ICMP, UDP Filtering | ○ | ○ | ○ | ○ |
| Blocking of abnormal IP packets | ○ | ○ | ○ | |
| Blocking of abnormal TCP packets | ○ | ○ | ○ | |
| Blocking of abnormal UDP packets | ○ | ○ | ○ | |
| Blocking of abnormal ICMP packets | ○ | ○ | ○ | |
| Blocking of LAND attack packets | ○ | ○ | ○ | |
| Defense against UDP flooding | ○ | ○ | ○ | |
| Defense against ICMP flooding | ○ | ○ | ○ | |
| SYN Flooding | ○ | ○ | ○ | |
| TCP Flooding | ○ | ○ | ○ | |
| HTTP Flooding | ○ | ○ | ○ | |
| Defense against Fragment Flooding | ○ | ○ | ○ | |
| L7 pattern check | ○ | ○ | ○ | |
| Defense against spoofed IP addresses | ○ | ○ | ○ | |
| Defense against DRDoS | ○ | ○ | ○ | |
| URL Behavior Anomaly | ○ | ○ | ○ | |
| Caching Behavior Anomaly | ○ | ○ | ○ | |
| DNS Query Flooding | ○ | ○ | ○ | |
| Defense against DNS Amplification attack | ○ | ○ | ○ | |
| Defense against SYN flooding | ○ | ○ | ○ | |
| Blocking of abnormal IP addresses | ○ | ○ | ○ | |
| Improved SSL performance (SSL offload) | ○ | |||
| HTTP acceleration and optimization (compression, cache, TCP reuse) | ○ | |||
| Load Balancing | ○ | |||
| Health Monitoring | ○ | |||
| GRE Tunneling | ○ | |||
| Full subnet protection without changes to the IP address (using BGP) | ○ |