Cloud web firewall that checks
vulnerabilities of website and responds to attacks
Web Firewall

It is a cloud web firewall that can be set up in various kinds of environments including on-premises environments, public clouds, private clouds, and hybrid clouds. Its speed and availability are excellent, providing safe protection from various web service security threats in a cloud environment. IXcloud provides s/w-type web firewall that can be installed and used on one VM, and stand-alone web firewall service that can be applied to multiple VM.
Contact an Expert
Price

| Category | Monthly Rate (VAT not included) |
|---|---|
| s/w web firewall | KRW 150,000 |
| Category | Type | Monthly Rate (VAT not included) |
|---|---|---|
| stand-alone web firewall + monitoring service |
300M (Single) | KRW 480,000 |
| 500M (Single) | KRW 600,000 | |
| 1G (Single) | KRW 960,000 | |
| 300M (HA) | KRW 960,000 | |
| 500M (HA) | KRW 1,200,000 | |
| 1G (HA) | KRW 1,920,000 |
* The monitoring service is provided by one of our partners, GABIA.
How to Use

Sign up for the service
- Select the web firewall type and service type and apply for the service.
Web Firewall installation
- KINX’s Operations Team will install a web firewall according to the service requested.
Configuration of security settings
- The security and monitoring service provider will contact you to configure the detailed security settings.
Web Firewall security
- After the security settings are configured, you will obtain the designated security services.
Configuration Diagram

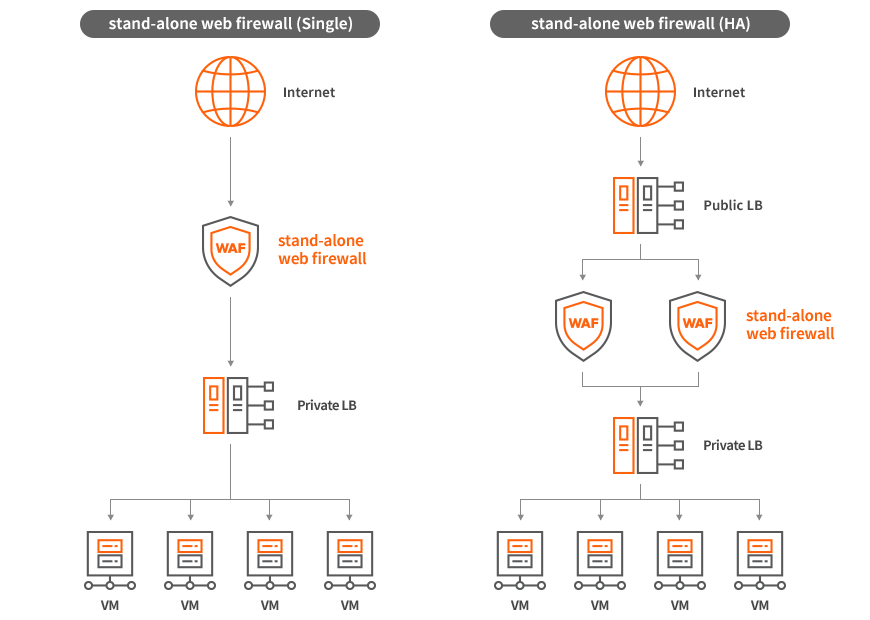
- Private LB requires separate configuration.
- When configuring Public LB, it is configured through IXcloud load balancer.
- Redundancy configuration is configured in Active – Active method.
Feature

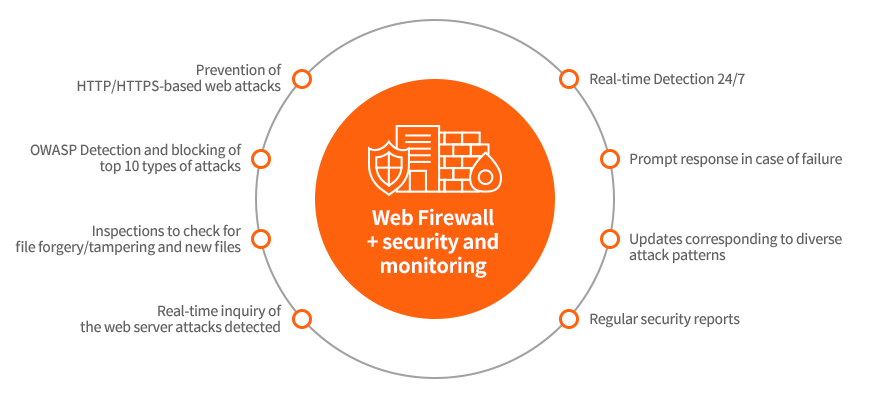
Detailed Features
- HTTPS/HTTP 1.0/1.1/2-based web attack response
- Detection and blocking of Layer7 DoS attacks, brute-force attacks and dictionary attacks
- Response to OWASP Top 10 and PCI DSS 6.6 requirements and top 8 vulnerabilities noted by the NIS
- Inspection of response data (detection of leakage of critical information)
- Inspection of uploaded files: Registration of binary (raw data) signatures
- Inspections to check for file forgery/tampering and creation of new files by path (URI)
- Security policy for open software (bulletin boards, online shopping mall solutions, blogs, etc.)
- Detection and blocking of file upload restrictions bypass attacks
- URI-based IP control (X-Forwarded-For identification)
Scope of Support

| Supported OS | Supported Web Server/Application |
|---|---|
| MS Windows (2003, 2008, 2012, 2016) |
· IIS 6.0, IIS 7.0, IIS 8.0, IIS 10 |
| Linux Kernel 2.6.x and higher (32bit, 64bit) |
· Apache 2.0, 2.2, 2.4 |
Recommended to

-

Companies that need to build a powerful security system in line with the latest security technology and trends
-

Companies that need to detect and block attacks on web vulnerabilities that are difficult to respond to with just firewalls and IPS/IDS
-

Companies that do not have any in-house employees to manage their servers